DAR Resources
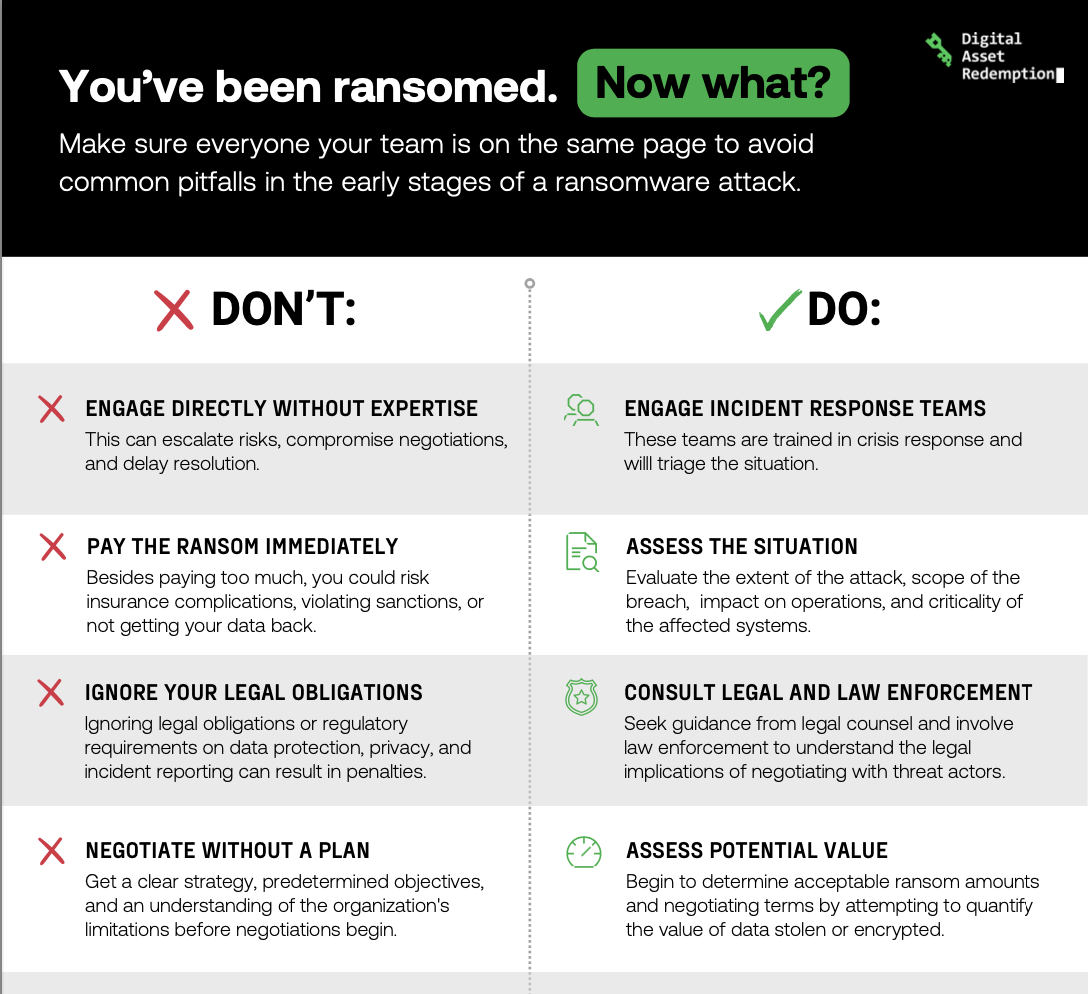
Dos and Don'ts of a Ransomware Attack
Your first steps of what to do – and not do – if you find yourself hit by ransomware.
Download
Whitepaper: "The Full Monti"
DAR's advanced threat actor attribution helps untangle the knot of sanctions restrictions in ransomware events
Download.png?width=1545&height=2000&name=DAR%20Inside%20Ransomware%20Negotiations(1).png)
Whitepaper: Inside Ransomware Negotiations
What goes into threat actor negotiations? Find out with this paper!
Download
Post-Event Dos and Don'ts
Some helpful reminders about how to move forward (and how not to!) after a ransomware event.
DownloadDon't see what you need?
Forgot where you put your asset? It happens all the time. Let us know what you need below and we'll be sure to send it along.